Seal Security wants to make open-source vulnerability remediation easy
Seal Security, a Tel Aviv-based startup founded by a group of former members of Israel’s Unit 8200 intelligence unit, is coming out of stealth today and announcing a $7.4 million seed funding round like by Vertex Ventures Israel, with participation from Crew Capital, PayPal Alumni Fund, and Cyber Club London.
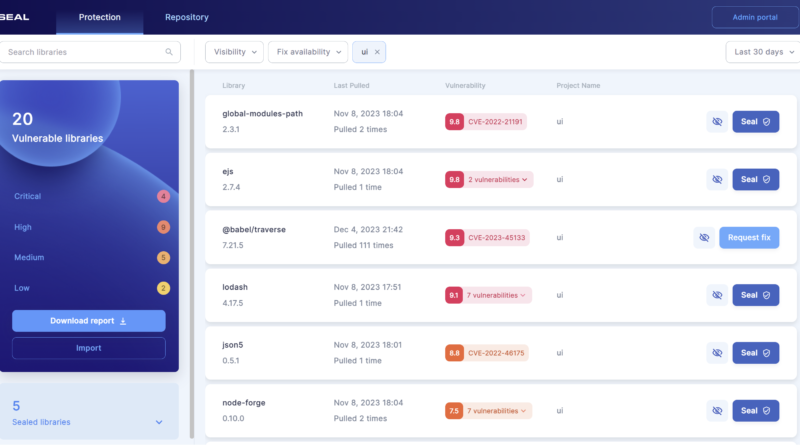
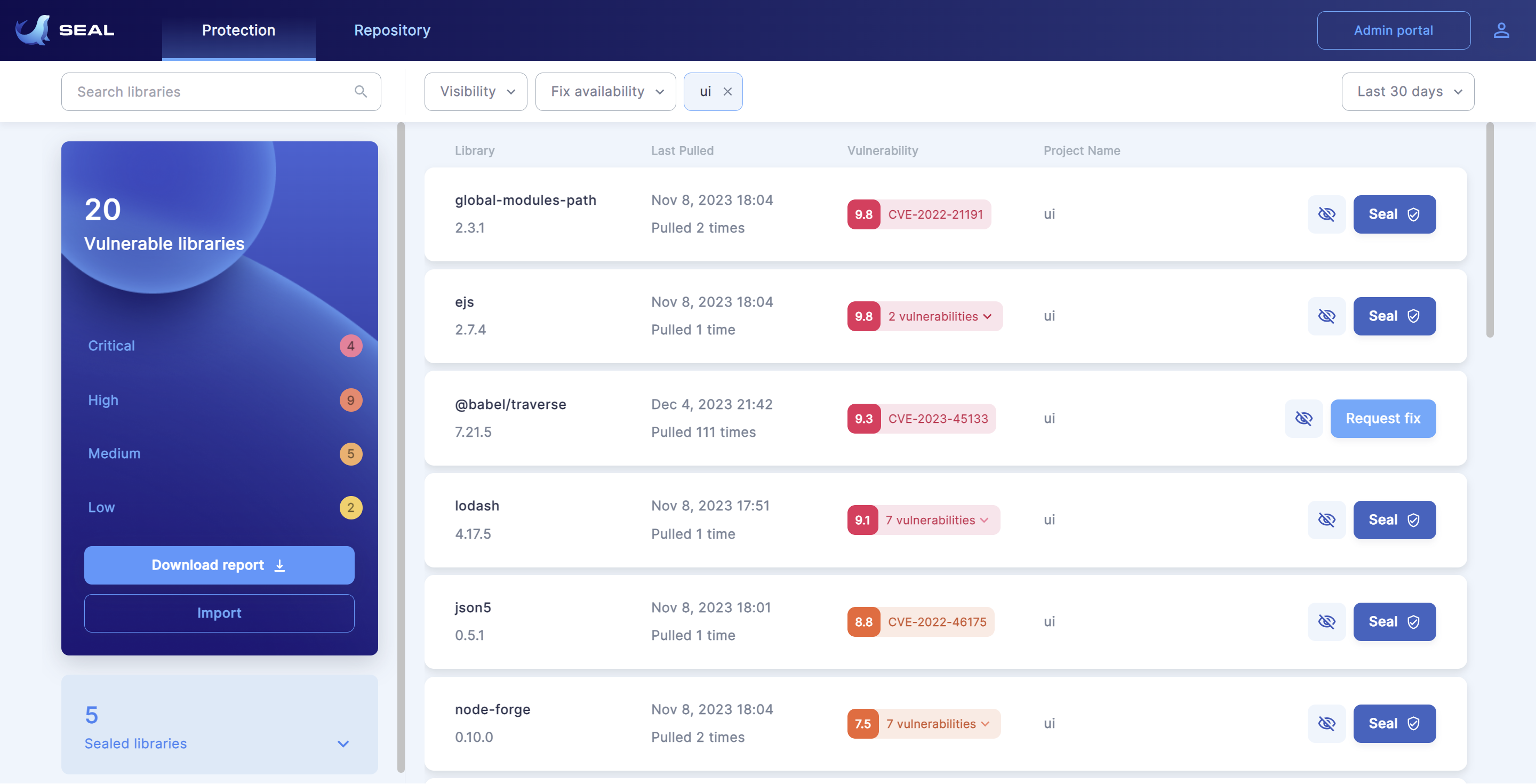
Ever since the Log4j vulnerability was discovered and the White House issued its software supply chain executive order, everybody who builds software knows about the importance of keeping the many open-source libraries they rely on up to date. But that’s often easier said than done, with large enterprises often employing entire teams that focus on nothing else but keeping their packages updated. In recent years, we’ve seen a number of security companies that specialize in alerting developers when one of their packages is vulnerable and while that’s valuable, the real work is in remediating these vulnerabilities, which in most cases simply involves installing an update.
Seal was founded by Itamar Sher (CEO), Lev Pachmanov (CTO) and Alon Navon (CPO). After their time in Unit 8200, the team members worked at various companies, including Cymmetria, Curv and PayPal. Sher tells me that the team joined forces in the summer of 2022.
“For me, it was really a matter of wanting to be a builder,” Sher said. “I spent some of the time being on the other side: being a researcher, hacking stuff, breaking stuff — which is fun in its own way. But I think one of the things that I cared about — and I really wanted to bring forward — is being more on the builder side.” As the first employee at Cymmetria, he already got a taste of that experience, but now as a founder and CEO, he is getting to see the full spectrum of the startup experience.
What makes Seal different is that it actually patches the vulnerable packages and doesn’t just update them. While working at PayPal, he realized that there was a lack of tools that could not just discover but also remediate security vulnerabilities. He also stressed that many of today’s tools bombard developers with hundreds of alerts, making it hard to prioritize which ones to focus on. In the end, these teams spend a large chunk of their time and energy on keeping packages updated (even those that may not even be used in production). “What we noticed is that for the majority of vulnerabilities that are out there, you can actually take the security patch that mitigates the risk and just apply it on the existing versions that the developers are using already,” Sher explained.
Currently, Seal Security integrates with GitHub to enable these patches in a company’s CI/CD pipeline. But what’s maybe more important is that Seal creates these patches itself. A lot of this process is automated and backed, in part, by using a large language model. These models, Sher explained, are very good at identifying the commit that introduced a given patch, for example. Indeed, without the models, a solution like Seal Security likely wouldn’t have been scalable only a couple of years ago.
“Open source components are foundational to software development, and organizations face significant challenges in managing libraries with critical vulnerabilities. These challenges have a significant impact on business outcomes,” explains Daniel Dines, the co-founder and general partner at Crew Capital (and the co-founder and co-CEO of UiPath). “Seal Security addresses this market demand with a solution that streamlines security patch management, allowing its customers to effectively eliminate vulnerabilities.”